You can use the “sapgenpse” command line tool to manage all PSE (Personal Security Environment) file operations easily on all operating systems.

Creating a PSE for the Server Using SAPGENPSE
We can use the option “get_pse" to generate the server’s PSE, which includes the public and private key pair and a public-key certificate.We can use this command with the options “noreq” or “onlyreq”
Following command generates a PSE is the SECUDIR directory.
sapgenpse get_pse <additional_options> [-p <PSE_name>] [-r <cert_req_file_name>] [-x <PIN>] [DN]
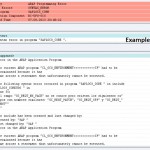
Example ;
sapgenpse get_pse -p F:\usr\sap\TST\ DVEBMGS00\sec\TST.pse -noreq -x tstpin “CN=TST, OU=Test, O=Company, C=TR”
Get Certificate Request Using SAPGENPSE
We can use “gen_pse” option with “sapgenpse” command to generate certificate request file for the related PSE file.
sapgenpse gen_pse <additional_options> [-p <PSE_name>]
Example ;
sapgenpse gen_pse –p F:\usr\sap\TST\DVEBMGS00\SAPSSLS.pse “CN=servername.net, OU=IT, O=Company, SP=Besiktas, L=İstanbul, C=TR”
This option created a new PSE file and the certificate request response, if we don’t want to create a new PSE file and just want to create a certification response as a file then
we can use the “-onlyreq” switch with “-r” file location information like below ;
sapgenpse gen_pse -p F:\usr\sap\TST\DVEBMGS00\sec\SAPSSLS.pse -onlyreq -r F:\usr\sap\TST\DVEBMGS00\sec\sapsslpse.req
Checking a PSE file Details Using SAPGENPSE
We can use “get_my_name” option with “sapgenpse” command to get the details of the related PSE file.
sapgenpse get_my_name <additional_options> [-p <PSE_name>]
Example ;
sapgenpse get_my_name -p F:\usr\sap\<SID>\DVEBMGS00\sec\SAPSSLS.pse
Creating the Server’s Credentials Using SAPGENPSE
We have to create server’s credentials “Cred_v2″ file under the SECUDIR with following command.
Example ;
sapgenpse seclogin -p F:\usr\sap\TST\DVEBMGS00\sec\TST.pse -O SAPserviceTST
as a result, the credentials file “Cred_v2″ for the user provided with the -O option is created in the SECUDIR directory.
Exporting the Server’s Certificate Using SAPGENPSE
Use the tool’s option “export_own_cert” to export the server’s certificate
sapgenpse export_own_cert -o <output_file> -p <PSE_name> [-x <PIN>]
Example ;
sapgenpse export_own_cert -0 tst.cer -p F:\usr\sap\TST\DVEBMGS00\sec\TST.pse
Maintaning the Server’s Certificate List Using SAPGENPSE
Use the tool’s option “maintain_pk” to maintain the server’s certificate list.
sapgenpse maintain_pk [<additional options>] [-a <cert_file>] [-d <number>] -p <PSE_name> [-x <PIN>]
Example ;
sapgenpse maintain_pk –p F:\usr\sap\TST\DVEBMGS00\sec\TST.pse –a tst.cer
Listing the Existing Certificate List Using SAPGENPSE
Use the tool’s option “maintain_pk” with the “-l” switch to maintain the server’s certificate list.
sapgenpse maintain_pk -p <PSE_name> -l (1 / 2 ..)
Example ;
sapgenpse maintain_pk –p F:\usr\sap\TST\DVEBMGS00\SAPSSLS.pse –l
sapgenpse maintain_pk –p F:\usr\sap\TST\DVEBMGS00\SAPSSLS.pse –l 1
Deleting the Server’s Credentials Using SAPGENPSE
Use the following command line to delete the server’s credentials ;
sapgenpse seclogin [-d] [-p <PSE_name>]
Example ;
sapgenpse seclogin -d -p F:\usr\sap\TST\DVEBMGS00\SAPSSLS.pse
Changing the PIN Using SAPGENPSE
Use the tool’s option “seclogin” to change the PIN that protects the server’s PSE.
sapgenpse seclogin [-chpin] [-p PSE_name>] [-x <PIN>] [-xn <new_PIN>]
Example ;
Old PIN –> 1
sapgenpse seclogin -p F:\usr\sap\TST\DVEBMGS00\sec\SAPSSLS.PSE -chpin -x 1 –xn